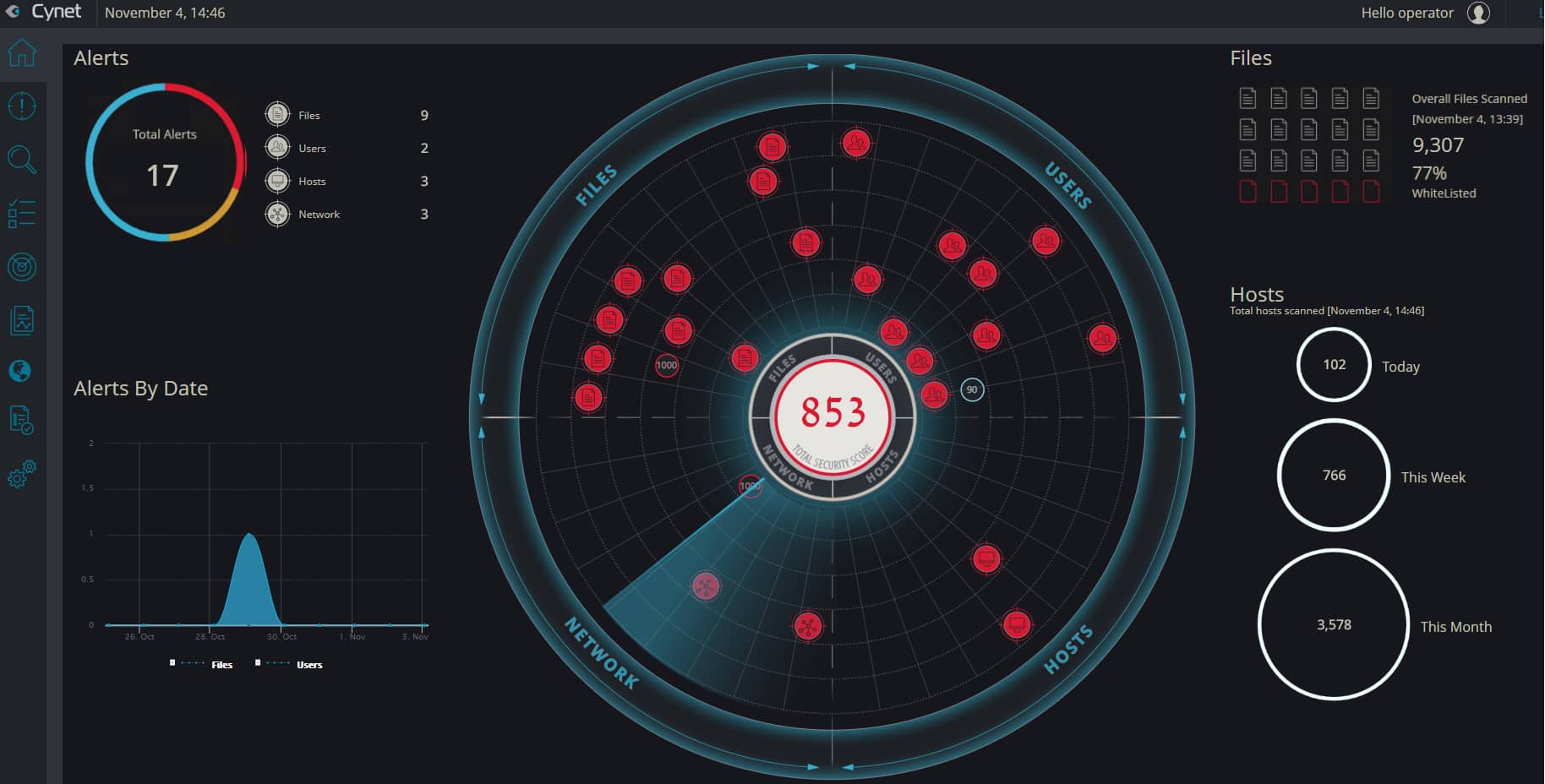
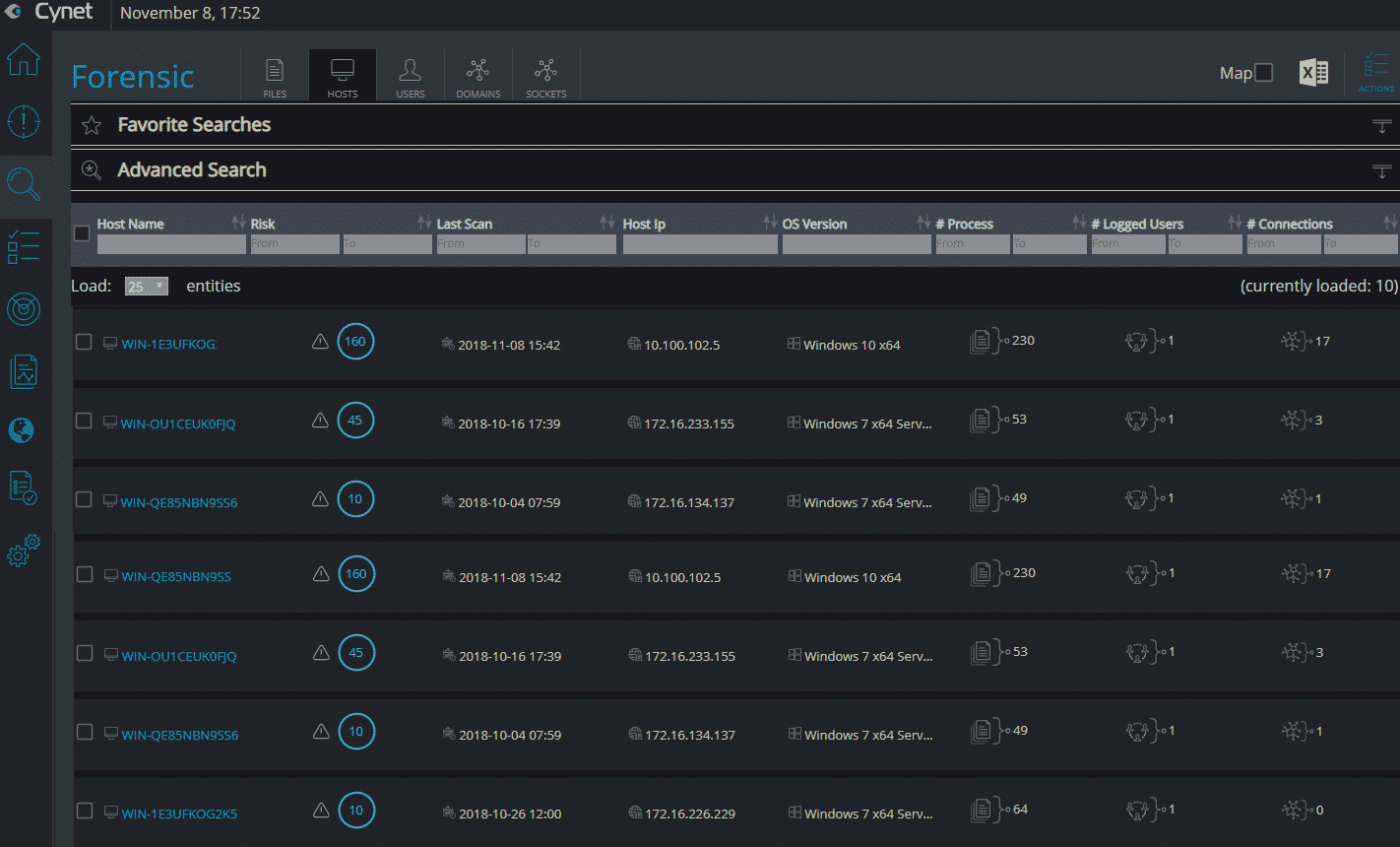
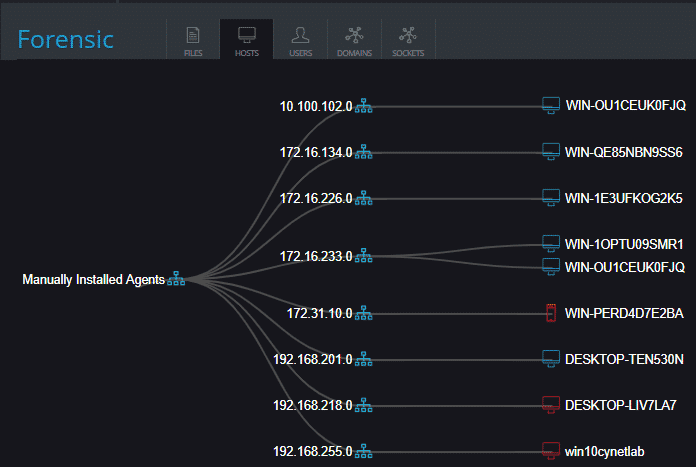
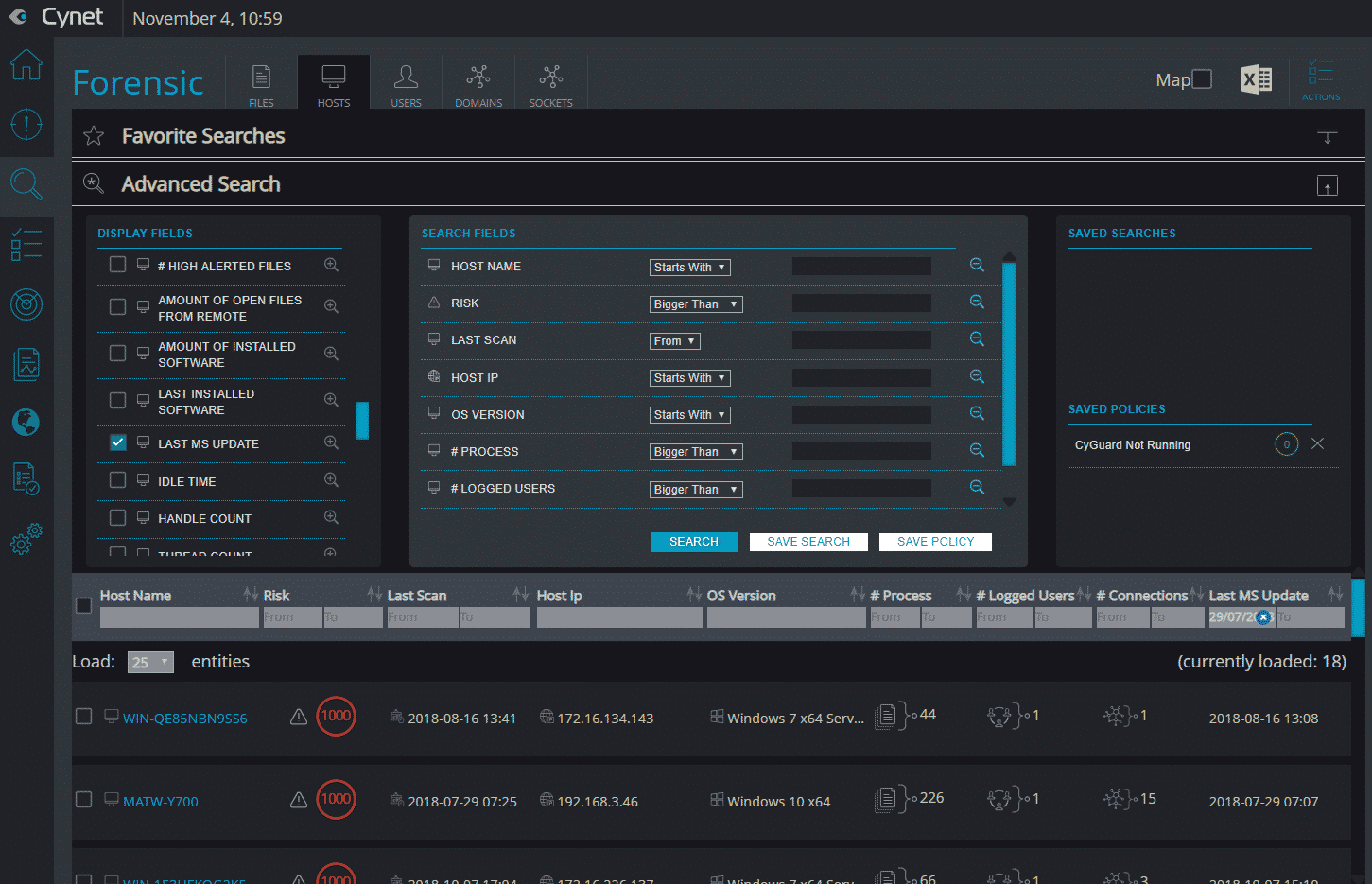
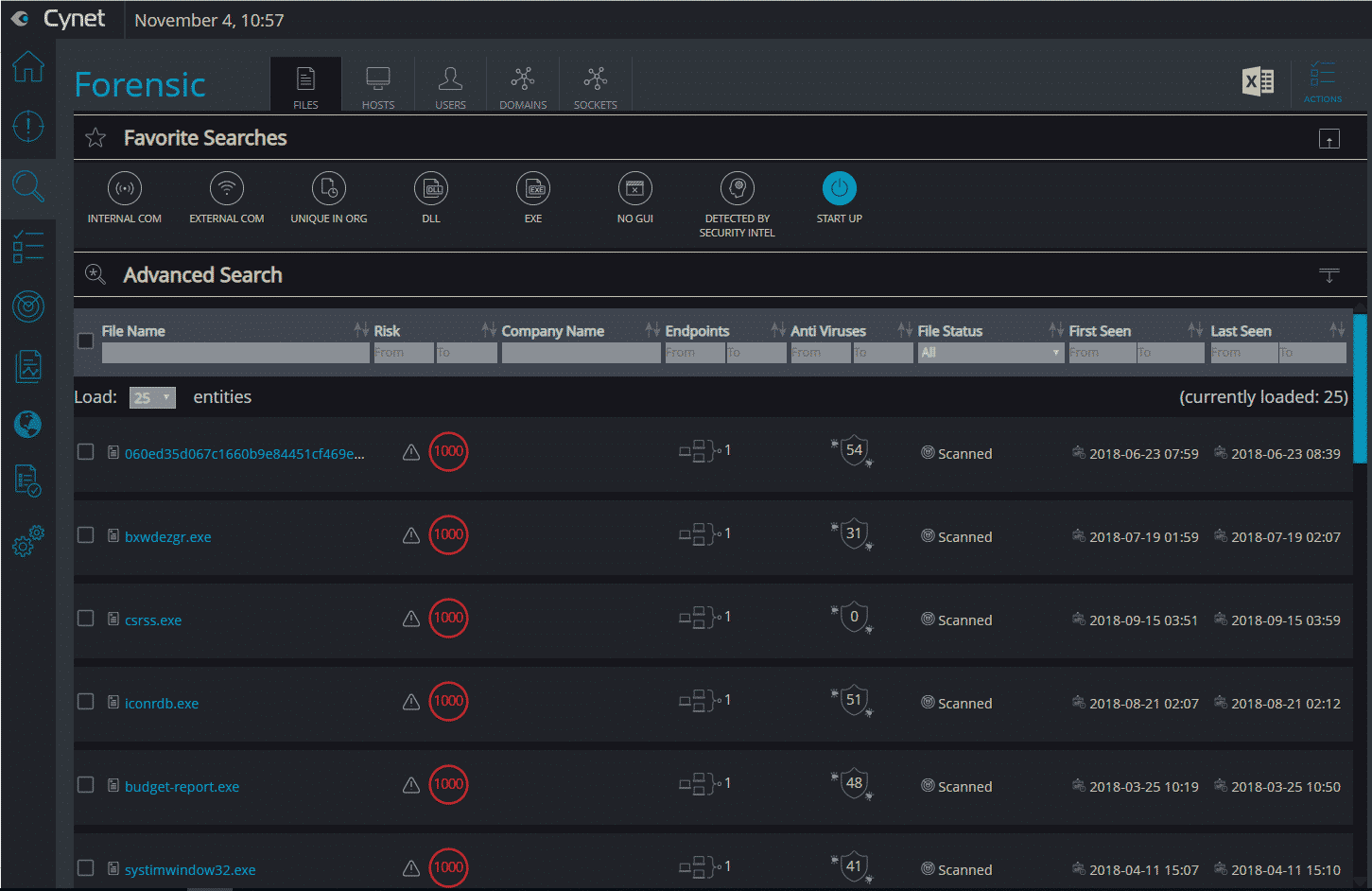
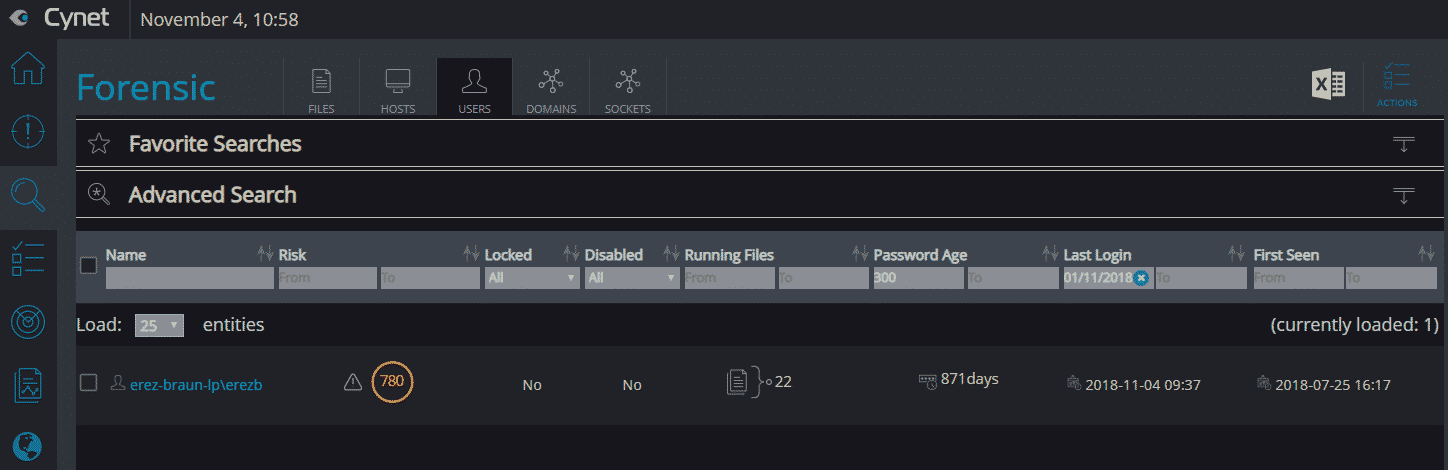
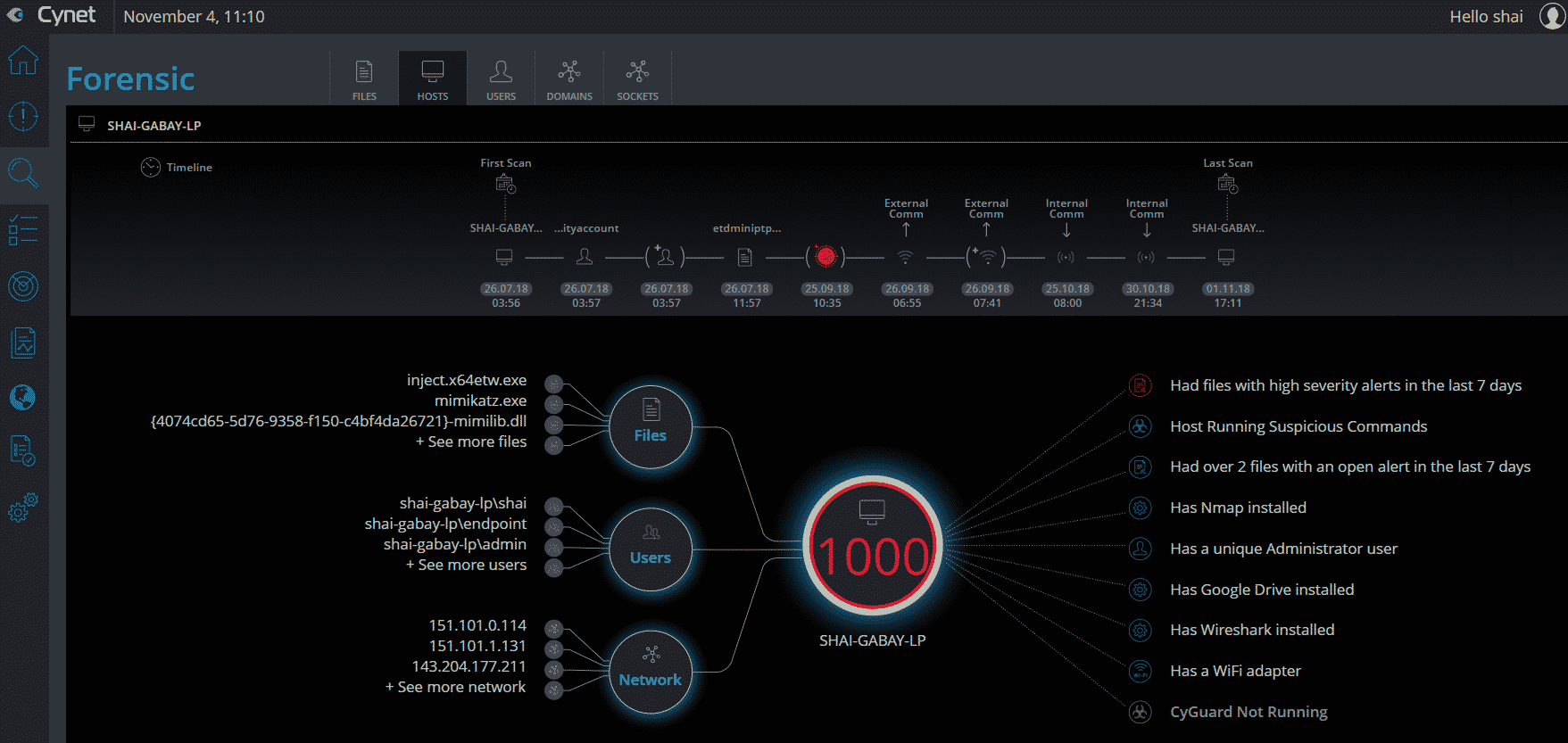
The autonomous platform is threat-agnostic, converging all the technologies and capabilities (including endpoint protection, EDR, network analytics, UBA and vulnerability management) to answer the visibility, prevention, detection and response needs of any-size organization. At the same time, it is easy and intuitive to deploy and manage. By that, the platform eliminates the need of complex multi-product security stacks, as well as the dependency on a highly skilled security workforce. Cynet built the platform to be simple and easy to deploy and use; provide broad visibility across the network, endpoints, files and users; protect against a very wide range of attacks including common as well as advanced, multi-layered attacks; and provide a team of security experts available 24/7 that complements whatever expertise you have in place. Deployed in Minutes Cynet includes very flexible deployment methods: On-premise, IAAS, SAAS, and hybrid mode. We evaluated Cynet using their SaaS version with a free trial across a broad spectrum of capabilities—deployment, visibility, prevention, detection, and response. Cynet installed quickly—in just a few minutes. We tried it on a few hundred endpoints. The speed and ease of the installation were remarkable. Total Environment Visibility: Host, Network, User, File Once installed, Cynet starts by mapping the entire internal environment: host configurations, executed files, network traffic and user activities. Cynet takes its broad view to correlate and connect behaviors, evidence, indicators, and anomalies to detect attacks. Very quickly, you get a dashboard of everything Cynet has uncovered: Within minutes, we could already see all live hosts: The immediate value Cynet provides is comprehensive visibility into the organization, including networks sources and destinations, installed applications, host inventory, and unpatched vulnerabilities. Cynet provides a network display of your internal environment with risky hosts marked in red and clickable for a deeper look: The other insights provided upon installation are centered around vulnerability management and compliance, in 4 main areas:
- OS Updates: Cynet checks the installed Windows patch and raises an indication if the patches are missing. In addition, Cynet creates an inventory of installed patches.
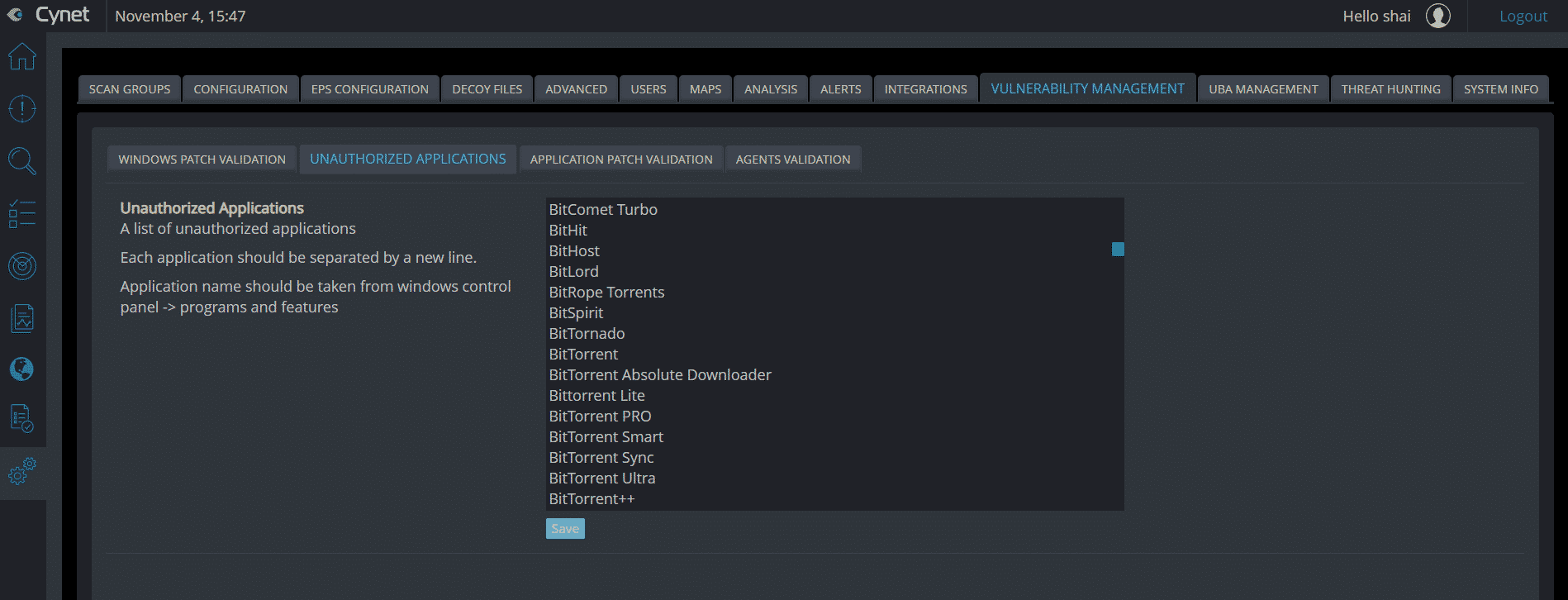
- Unauthorized applications: Cynet provides a list of blacklisted applications that can be customized and alerts if such applications are found. As part of the simplicity of the platform, every object is clickable and once clicked, all data is presented in a simple way on a single timeline, with all the associated history and objects: Mature security teams can also leverage all data being collected by Cynet through a fully-documented rest API. Prevention Prevention of Files\Running processes Cynet utilizes multiple prevention layers to either prevent execution altogether or kill malicious processes in runtime:
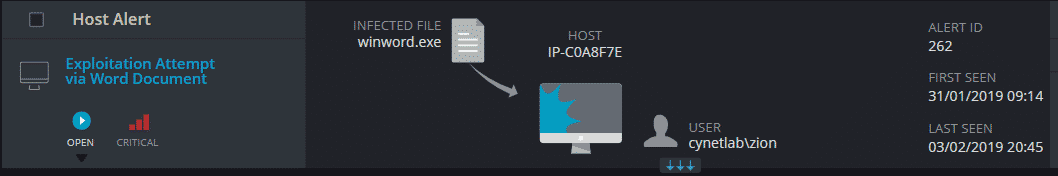
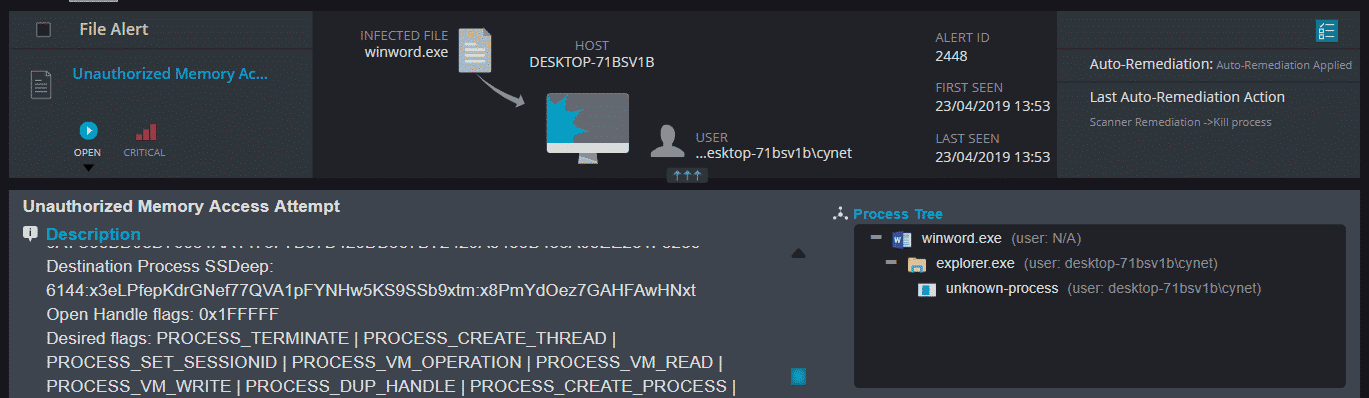
Known Malware – Identify and prevent the execution of malware with known signatures. Machine learning based NGAV – Analyze files before execution using unsupervised machine learning to discover malicious attributes. Threat Intelligence – Over 30 live feeds of various Indicators of Compromise. Fuzzy Hashing – Identify files with high similarity to know malware hashes. Memory Access Control – Ensure only legitimate processes can gain access to critical areas in memory. Behavioral Analysis – Monitor process at runtime and terminate upon detection of malicious behavior.
Figure 10: prevention example 1, behavioral analysis
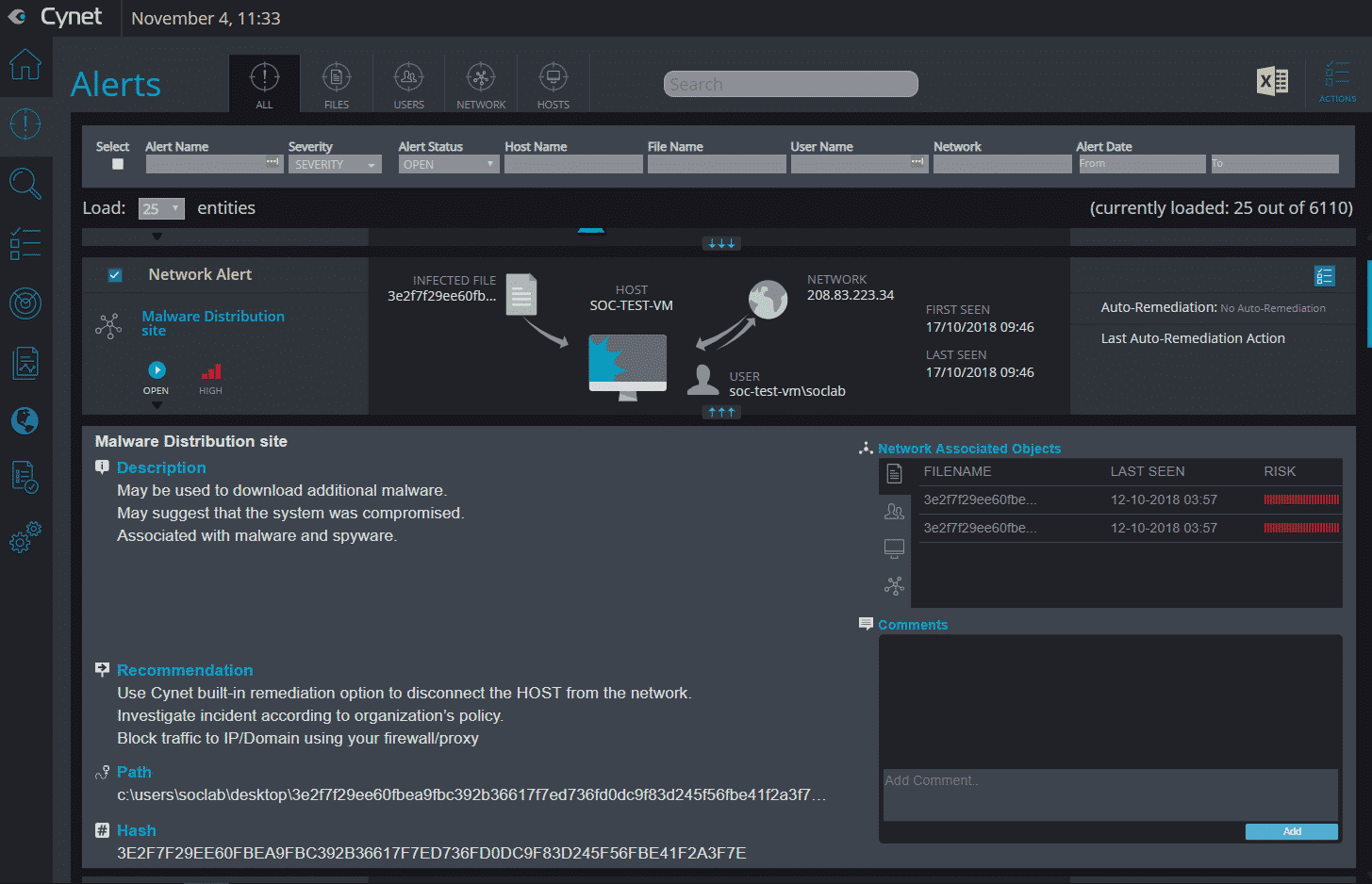
Figure 11: prevention example 2, memory monitoring Prevention of Malicious Network Traffic Cynet detects a wide range of network-based attacks such as ARP poisoning, DNS responder, tunneling attacks and others. Alerts can be configured to apply automated traffic blocking, elevating protection from detection to proactive prevention. Detection Cynet’s approach to security is about convergence. Namely, Cynet not only brings together detection, correlation and automation—but unlike point solutions—Cynet also converges its analysis across endpoints, for users, files and networks. In addition to traditional endpoint security, Cynet’s detection capabilities also include EDR, UBA, deception and network analytics. When seeing a live demo of the capabilities for the first time, it’s impressive to see the variety of alerts that can be generated – such as malicious behavior, exploitation, ransomware, lateral movement, brute force, user login anomalies, DNS Tunneling, privilege escalation, credential theft and more, which are the result of the multiple detection layers that Cynet includes. Cynet prioritizes the alerts and makes them easy to understand and act upon—by pre-correlating all related objects into one single view of the alert, highlighting actionable information, and presenting additional information and recommendations with a click of a button. Everything is wrapped in a simple, self-explanatory interface that can be used by anyone with a minimal level of expertise: In addition to the comprehensive detection, Cynet claims to have a very low false-positive ratio, as a result of the multi-layered approach. Response Cynet provides advanced and comprehensive response capabilities for the hosts, users, files or networks. For example:
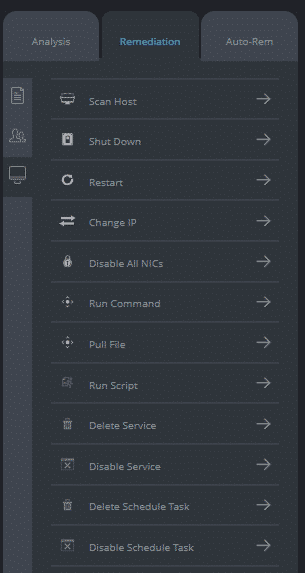
Kill, delete or quarantine malicious files. Disable users and run commands. Shut down the process or restart hosts. Isolate or block traffic.
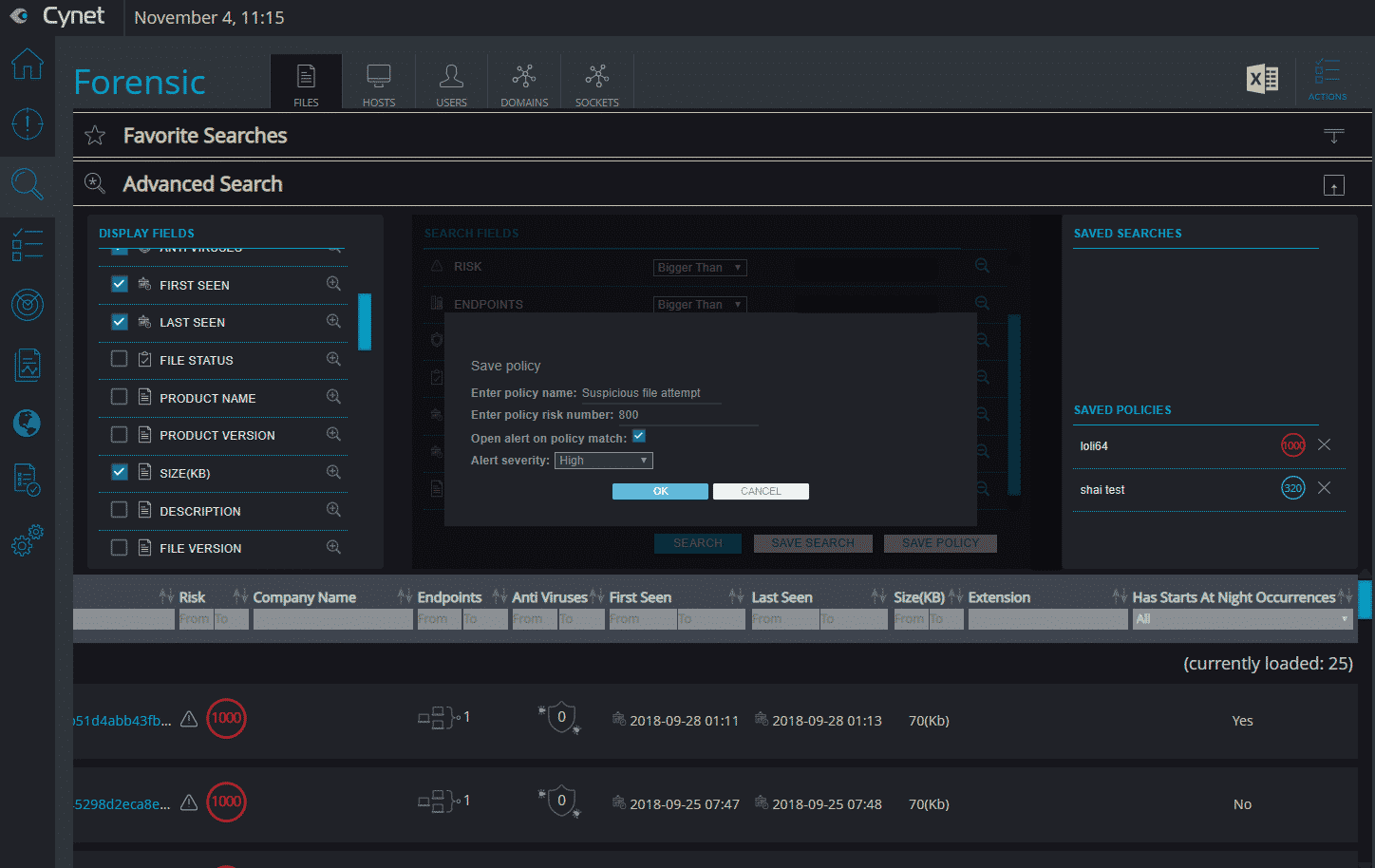
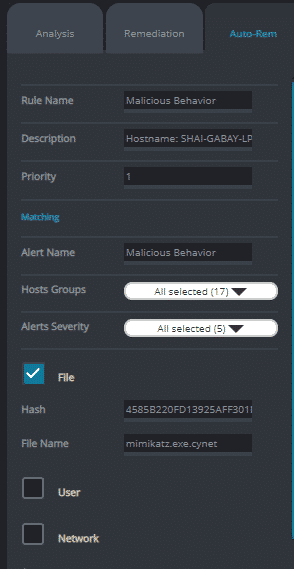
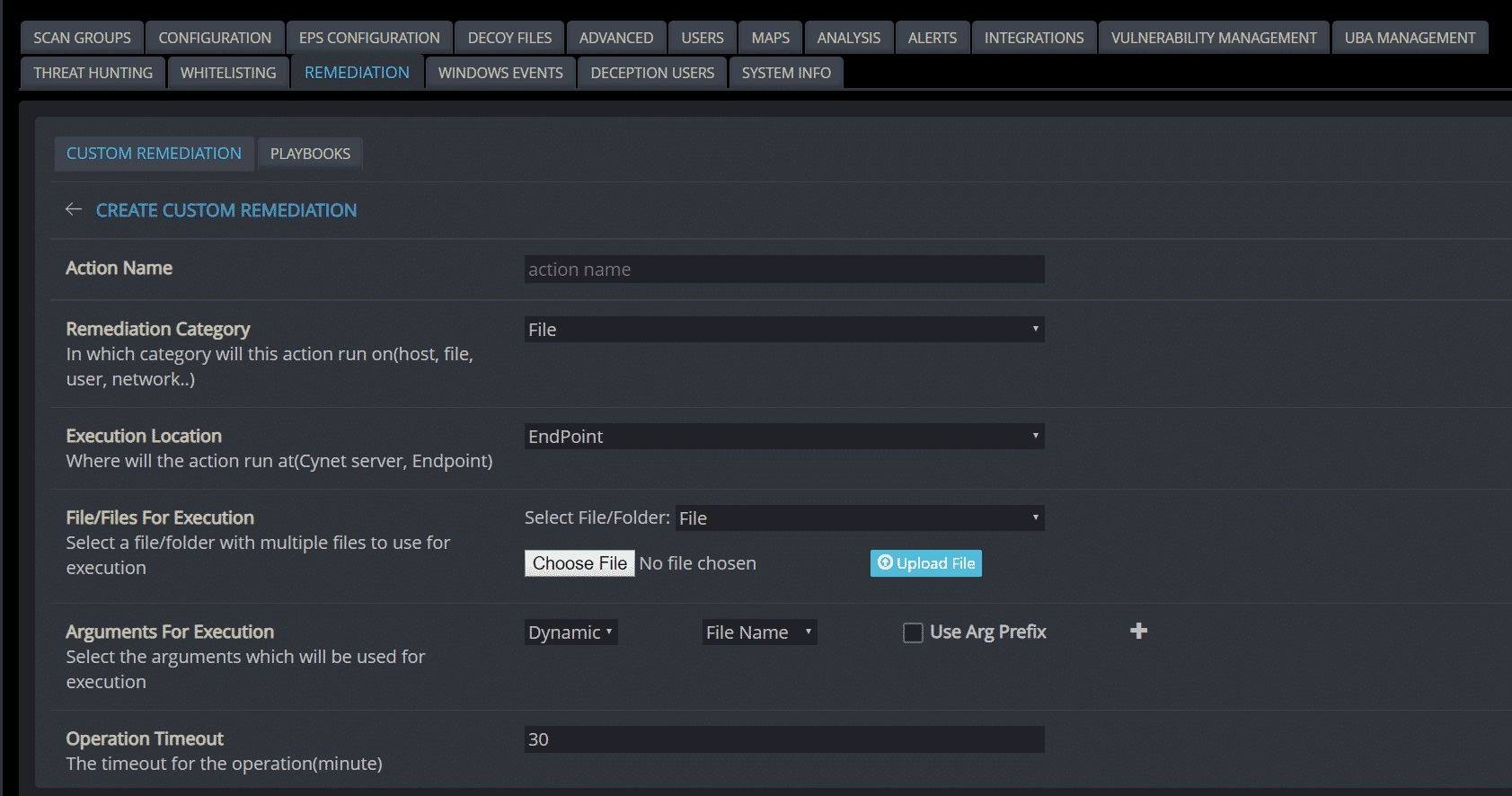
Automated Response: For each alert Cynet creates, the user can create and customize his own automatic remediation rule, to improve the incident response process and the prevention of a real-time threats. As part of this, Cynet provides a comprehensive rule creation mechanism that allows the user to customize the action according to the organization’s needs, such as: to which group to apply the rule, whom to exclude, etc. In addition, Cynet enables its user to tailor custom remediations, chaining together various remediation actions and uploading scripts that communicate with firewall, DC, etc. for a wider response orchestration.
Figure 15: custom remediation configuration CyOps – a 24/7 Security Team Cynet includes CyOps – a 24/7 security operations team – at no additional cost, to complement the expertise that their customers lack. What do you get? It’s not a watered-down service that incurs hidden costs if you go above a certain threshold. It’s a proactive service – if there something you should care about, a threat you missed, or if you need to perform forensics or hunt for threats—someone contacts you. Their service includes:
Forensics: In the event of an incident, Cynet experts perform breach post mortems. Malware analysis: Cynet malware reverse engineers analyze malware samples to get full attack life-cycle, origin and potential impact of malware, quickly identifying threat actors, motivations and likely targets. Threat hunting: Cynet’s crowd-sourced intelligence from the customer ecosystem provides the unparalleled ability to uncover advanced threats across users, endpoints, files, and networks.
Conclusion Cynet is banking on an industry moving from fragmentation to consolidation. From the looks of what they’ve assembled, they may be onto something big. For organizations that do not have the resources and security expertise of a Fortune 500 company, we see Cynet as the ideal solution – its rapid deployment, single-pane-of-glass approach, and multiple technology capabilities is a real game changer. If your organization is 300 endpoints or less, we recommend signing up for Cynet’s SaaS free trial: https://saas.cynet.com/signup. If your organization is larger, we suggest requesting a demo to get a personal walkthrough of the platform: https://www.cynet.com/request-a-demo/.