Link to MiniDuke
According to the researchers, the threat has been in circulation since at least October of 2013. In addition to Tor, the malware was also distributed through pirated softwares hosted on many torrent sites. However, F-Secure believes the OnionDuke family is much older and linked to MiniDuke, since they have found evidence to suggest that the samples they have analyzed are actually version 4 of the malware. Researchers haven’t yet identified any of the older versions, but the timestamps on the oldest OnionDuke binaries they have analyzed were from July 5 and July 15, 2013.
Link to MiniDukePropagation & Components
The “MiniDuke” gang, which previously infected government agencies and organizations in 23 countries with highly advanced malware that uses low-level code to stay hidden. MiniDuke was intriguing because it bore the hallmark of viruses first encountered in the mid-1990s, when shadowy groups such as 29A engineered innovative pieces of malware for fun and then documented them in an E-zine of the same name. Written in assembly language, most MiniDuke files were tiny. Their use of multiple levels of encryption and clever coding tricks made the malware hard to detect and difficult to reverse engineer. The code also contained references to Dante Alighieri’s Divine Comedy and alluded to 666, the “mark of the beast” discussed in the biblical Book of Revelation. OnionDuke is however, a different family from MiniDuke. The co-relation was found because both seemed to use the same command & control chain.
Propagation & Components
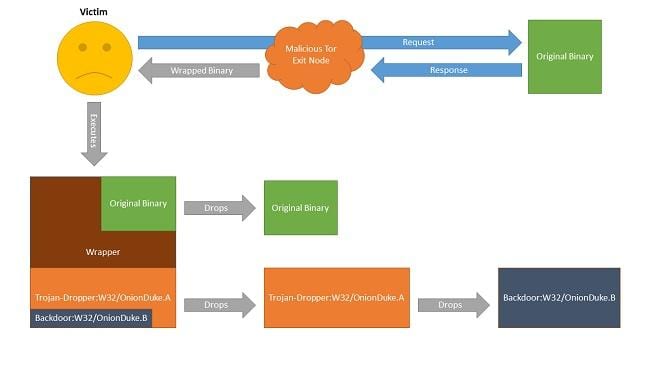
In the research carried out, it appears that the attackers used Tor Anonymiser Network Nodes to spread the malware dropper Trojan-Dropper:W32/OnionDuke.A. The dropper contains a PE resource that appears to be an embedded GIF image file, but in reality it’s a DLL file that’s decrypted, written to the disk, and executed. The DLL file, detected as Backdoor:W32/OnionDuke.B, decrypts the embedded configuration file and attempts to connect to the hardcoded Command & Control domains specified in it. “From these C&Cs the malware may receive instructions to download and execute additional malicious components. It should be noted, that we believe all five domains contacted by the malware are innocent websites compromised by the malware operators, not dedicated malicious servers,” F-Secure’s Artturi Lehtiö wrote in a blog post. Another component discovered by F-Secure is the Backdoor:W32/OnionDuke.A. which contains the domains of the command and control hardcoded within it. This is what led F-Secure to make the connection to MiniDuke. Attackers also believe that Twitter is also being used as an addition command channel. This attack was targeted at mostly Tor users in European countries. The aim seems to be a country within the sphere of influence of Russia, put bluntly, Ukraine. However, experts haven’t been able to determine the distribution vector utilized in these attacks.”Interestingly, this would suggest two very different targeting strategies. On one hand is the ‘shooting a fly with a cannon’ mass-infection strategy through modified binaries and, on the other, the more surgical targeting traditionally associated with APT operations,” Lehtiö said. The same group also discovered another version of the malware, labelled CosmicDuke. Tor officials have long counseled people to employ a VPN when using the privacy service, and OnionDuke provides a strong cautionary tale when users fail to heed that advice.